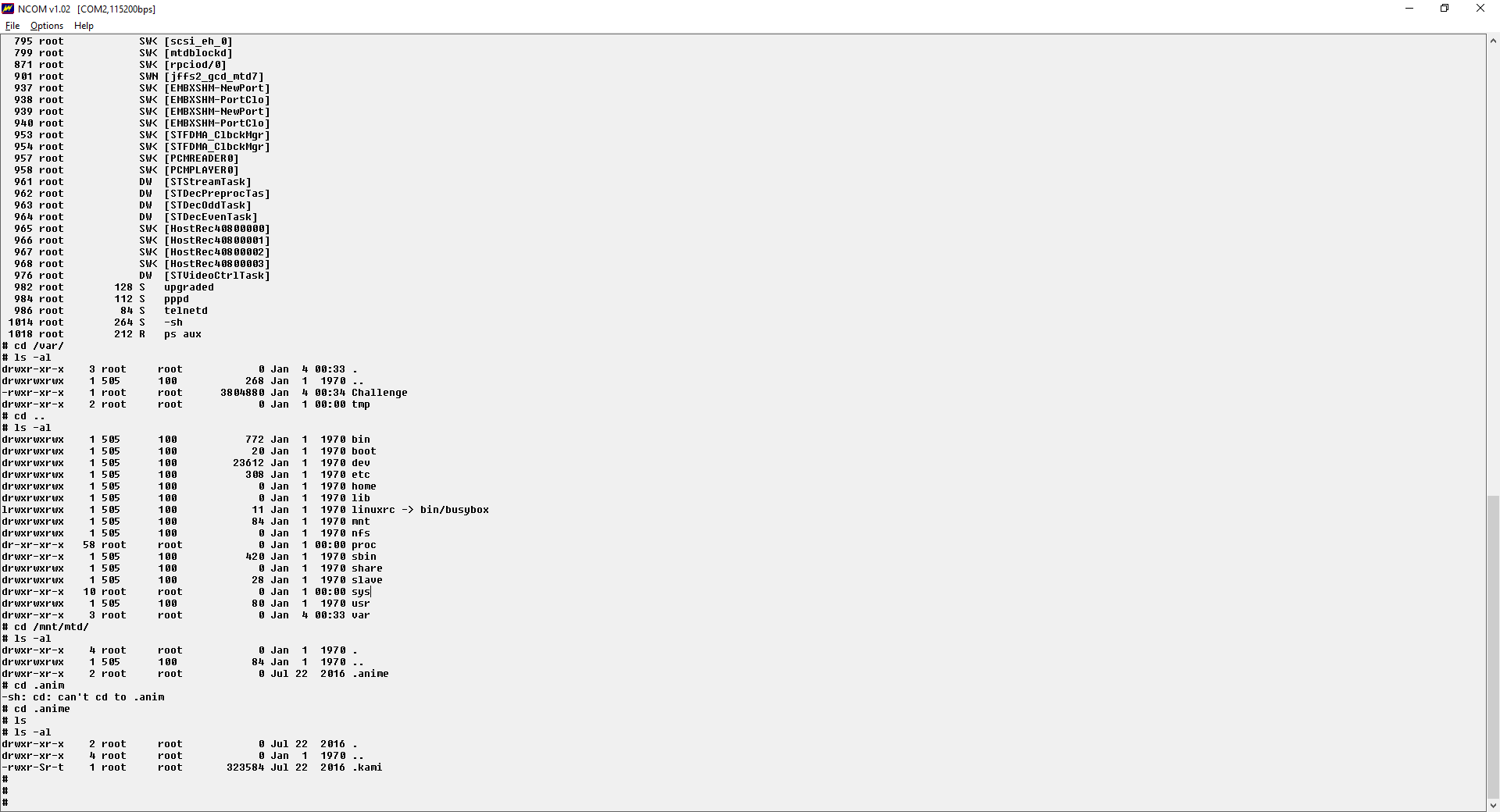
During August 2016, we came across several devices that were infected with a new malware that we couldn’t identify – for now. It resides in a read-write partition of some CCTV devices (most partitions on these devices are read-only), in a folder called .anime under the name .kami. It seems the attack used hard-coded telnet credentials and then downloaded the now-unknown malware(or maybe created the file via ”echo” commands).
We failed to identify it, since it’s truncated – the final file seems to be bigger than the partition it was created on (mounted as /mnt/mtd).
.kami: ERROR: ELF 32-bit LSB executable, Renesas SH, version 1 (SYSV), statically linkederror reading (Invalid argument)
The MD5 of it:
cdd887f2112b3d87b96154ca492368a8 .kami
For now, all we can recommend is to move devices from DMZ to proper port-forwarding and, where needed, install a router as a firewall in front of them.